Do you have any idea about what occurs in the engine of your CI? Without profound comprehension, you may be powerless against creative inventory network assaults. This article depicts such an assault.
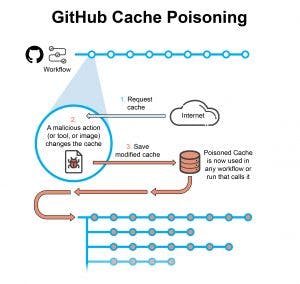
Reserving is utilized to accelerate processes. Rather than building or downloading, over and over, a bundle, it basically and consequently saves relics for reuse. Notwithstanding, reserves may be harmed. For example, a vindictive device utilized in a test work process can harm its reserve. Afterward, another work process utilizing a similar store may be impacted. In the event that this work process has higher honors, this is as a matter of fact a strategy for turning an assault. Here, we report on a trial assault on a GitHub CI pipeline, however a comparable sensible weakness exists in other CI items.
The assault works out as follows:
An assailant distributes a malignant device or a Github Action which is gotten by a clueless work process in Github.
The work process is planned with a store
The vindictive payload alters the store to incorporate noxious information.
Different work processes that approach this store starting here may be impacted.
Because of our divulgence, GitHub said they don't have an arrangement to solidify the store include against this kind of assault.
We propose moderation by marking the store's substance hash esteem cryptographically and checking the mark before use. To get more familiar with the assault and alleviations, keep reading.GitHub Cache Poisoning.
GitHub Cache
frequently reuse similar results or downloaded conditions starting with one run then onto the next (for instance, the bundles downloaded by bundle and reliance the board instruments like Maven, Gradle, npm, and Yarn. These bundles are generally kept in a nearby store of downloaded conditions).
To improve CI runs, GitHub awards admittance to a store asset that can be utilized across the pipeline by means of an API. The sections in the reserve are a key-esteem blend, where keys are string-based, and esteems are documents or registries one might want to store.
Utilizing the activity/reserve Git activity anyplace in the CI will run two stages: one stage will occur during the run cycle when it's called and the other will happen post work process (in the event that the run activity returned a store miss).
Run activity - is utilized to look and recover the reserve. The pursuit is finished utilizing the store key, with the outcome being either a reserve hit (achievement, information tracked down in reserve) or reserve miss. Whenever found, the documents and indexes are recovered from the reserve for dynamic use. On the off chance that the outcome is store miss, the ideal records and catalogs are downloaded as though it was whenever they first are called. Post work process activity - utilized for saving the store. On the off chance that the consequence of the reserve bring in the run activity returns a store miss, this activity will save the present status of the registries we need to reserve with the gave key. This activity happens naturally and needn't bother with to be expressly called.
GitHub Cache Permissions
frequently reuse similar results or downloaded conditions starting with one run then onto the next (for instance, the bundles downloaded by bundle and reliance the executives instruments like Maven, Gradle, npm, and Yarn. These bundles are typically kept in a nearby store of downloaded conditions).
To streamline CI runs, GitHub awards admittance to a store asset that can be utilized across the pipeline through an API. The sections in the reserve are a key-esteem blend, where keys are string-based, and esteems are documents or catalogs one might want to store.
Utilizing the activity/store Git activity anyplace in the CI will run two stages: one stage will occur during the run cycle when it's called and the other will happen post work process (on the off chance that the run activity returned a reserve miss).
Run activity - is utilized to look and recover the store. The pursuit is finished utilizing the store key, with the outcome being either a reserve hit (achievement, information tracked down in store) or store miss. Whenever found, the records and indexes are recovered from the reserve for dynamic use. In the event that the outcome is reserve miss, the ideal documents and registries are downloaded as though it was whenever they first are called. Post work process activity - utilized for saving the store. In the event that the consequence of the store bring in the run activity returns a reserve miss, this activity will save the present status of the catalogs we need to reserve with the gave key. This activity happens naturally and needn't bother with to be expressly called.
GitHub CI Scoping
- Virtual Machine (VM) for each work
- Work authorizations
- Work process scopes
- Work process runs
- Git branches
- Work process character tokens
- GitHub store scope has been characterized in a manner that can break a portion of the other degree limitations (ex: GitHub reserve can influence different work processes).
The Attack
We utilized a model CI that included two work processes. This model demonstrates the way that an assault can turn from a low consent work process to a high consent one.
Unit-test work process running unit-test and code inclusion apparatuses. We accept that one of the apparatuses is pernicious or defenseless against remote code execution. The work process necessities to utilize the activity/reserve Git activity. Any work process can get to the store. Discharge work process assembles and delivers the application antiquity. This work process utilizes a store to upgrade utilizing the Golang conditions. The unit-test work process utilizes a noxious activity that adds a reserve section with pernicious substance by changing a Golang logging library to add the string, 'Terrible library' to the application curio portrayal.
Then, the delivery work process utilizes this harmed store section. Accordingly, the malignant code is infused into the assembled Golang double and picture. The reserve remains harmed until the passage key is disposed of (for the most part set off by reliance refreshes). A similar harmed reserve will influence some other work process, run, and kid branch utilizing a similar store key.
GitHub Disclosure
Github's reaction to our divulgence was that the Git activity, activity/reserve acts true to form and they have no designs to fix the perusing of the store. Albeit the GitHub group doesn't consider this conduct tricky, we inform DevSecOps experts to be attentive regarding this assault vector.
##Mitigations
Try not to involve stores in that frame of mind in significant work processes.
Run your work processes successively, with the believed work process running first to ensure your store is made in a confided in work process.
Merchant your conditions - Vendoring in GoLang is a technique for guaranteeing that all outsider bundles utilized in the Go task are steady for every individual who produces for that application. Like that, reserved conditions will stay substantial for all parts of the task. Different dialects probably won't uphold this strategy.
Sign the store esteem cryptographically and check the mark before use.
Copyist mitigates such goes after by granularly marking any item or registry in a work process like a reserve. Before the delivery, you can utilize Scribe to approve that main a reserve produced by a believed work process was utilized to fabricate the delivery.
